Development of OrganoBait synthetic bait, the NSF-Supported projected from Kepley BioSystems to provide an ocean-restorative alternative bait product
Technology topic
Cybersecurity and Authentication (CA)
The Cybersecurity and Authentication topic focuses on innovations related to the security and integrity of data and data processing and the authentication of people and devices. These subtopic areas are meant to serve as examples; all proposals with technical innovation and significant commercial potential are welcome, regardless of the specific area of focus of the project.
Sub-Topics
CA1. Computation on Encrypted Data
CA2. Cryptography, including Post-quantum Cryptography
CA3. Data Privacy and Integrity
CA4. Device Authentication
CA5. Distributed Ledger
CA6. Encryption, including Homomorphic Encryption
CA7. Network and Device Security
CA8. Personal Authentication
CA9. Secure and Trusted Computing
CA10. Secure Machine-to-Machine Communication
CA11. Security of Cloud and High Performance Computing (HPC) Platforms
CA12. Other Cybersecurity and Authentication Technologies
Application process for Cybersecurity and Authentication (CA) funding
Eligibility for Cybersecurity and Authentication (CA) funding +
- Your company must be a small business (fewer than 500 employees) located in the United States.
- At least 50% of your company’s equity must be owned by U.S. citizens or permanent residents. NSF does not fund companies that are majority-owned by multiple venture capital firms, private equity firms, or hedge funds, to participate in SBIR and STTR.
- All funded work, including work done by consultants and contractors, needs to take place in the United States.
- The project’s principal investigator (tech lead) must be legally employed at least 20 hours a week by the company seeking funding. The principal investigator doesn’t need any advanced degrees.
- The principal investigator needs to commit to at least one month (173 hours) of work on a funded project per six months of project duration.
Evaluation Criteria: What We Look for When Evaluating Cybersecurity and Authentication (CA) proposals +
- Technological Innovation
- Broader Impacts
- Commercial Potential
- Read more about our criteria
Take our project assessment to see if your work might be a good fit for NSF funding.
Featured Companies
Monitoring internal and external network performance - ThousandEyes

Mohit Lad, CEO & Co-Founder of ThousandEyes
“The grants we received from NSF were instrumental in bootstrapping ThousandEyes and allowing us to focus on building the first version of our product and acquiring customers. By the time we raised our series A from Sequoia capital, we had a handful of well-known brands as customers with annual bookings of more than $250k, i.e. real revenue. Thanks to NSF, we were on our way to commercializing our technology.” -Mohit Lad, CEO & Co-Founder of ThousandEyes, a network intelligence platform for businesses, was founded by Lad and Ricardo Oliviera in 2010. In 2018, they have 220 employees and have raised nearly $110 million.
ThousandEyes delivers Network Intelligence—performance visibility and actionable insights on digital experience for every user and application over any network. It arms network engineers, operations teams, support/service desk staff, developers, and even business users with an accurate, up-to-the-moment understanding of the link between application delivery and underlying network dependencies and behaviors– both inside and outside the organization.
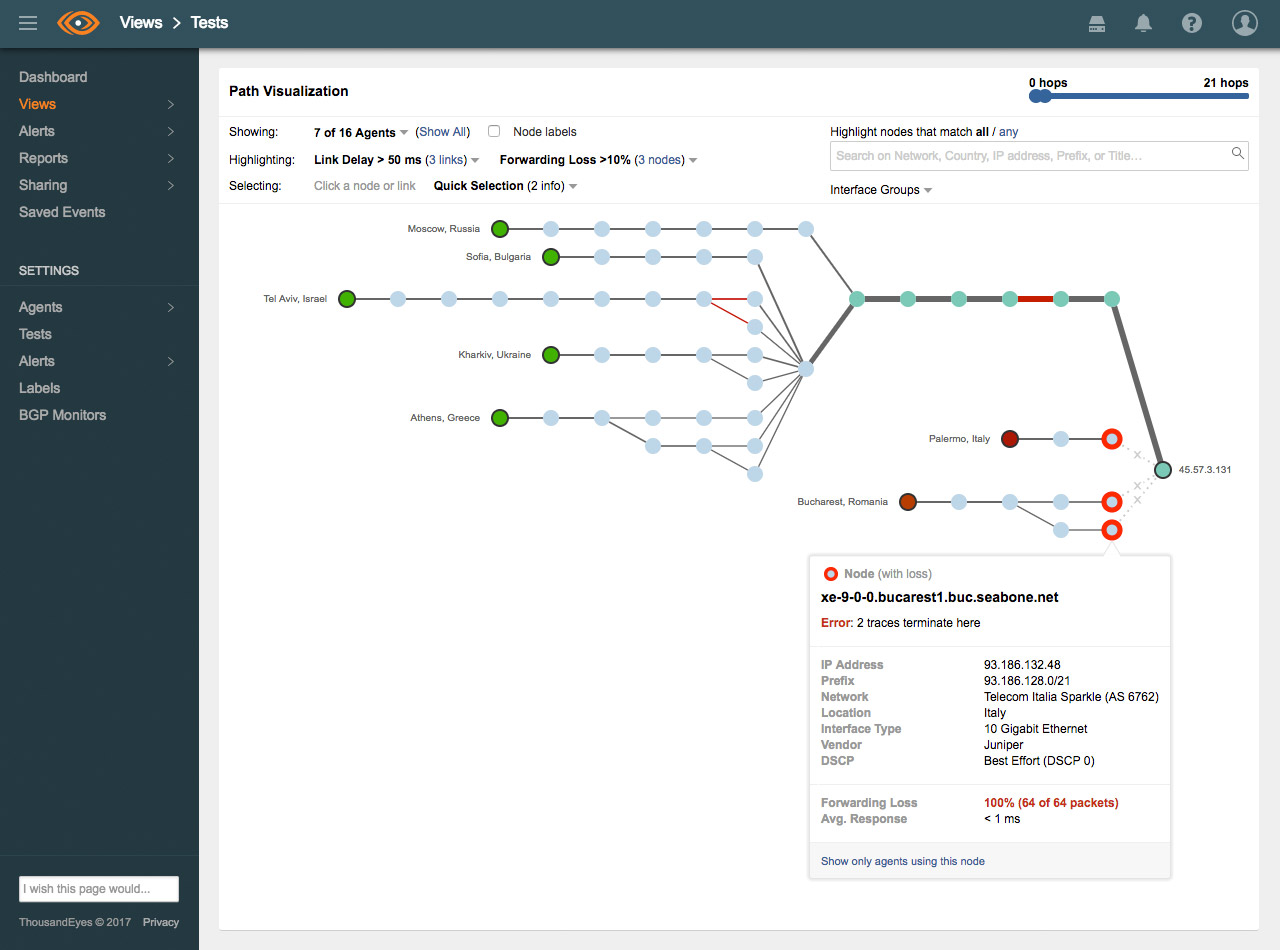
ThousandEyes' patented Path Visualization provides detailed hop-by-hop visibility and performance metrics from any network, even if it's outside your enterprise boundaries. A global inference engine correlates multiple streams of data and visually pinpoints the location of outages (shown as red circles), and provides additional contextual information about the specific location.

